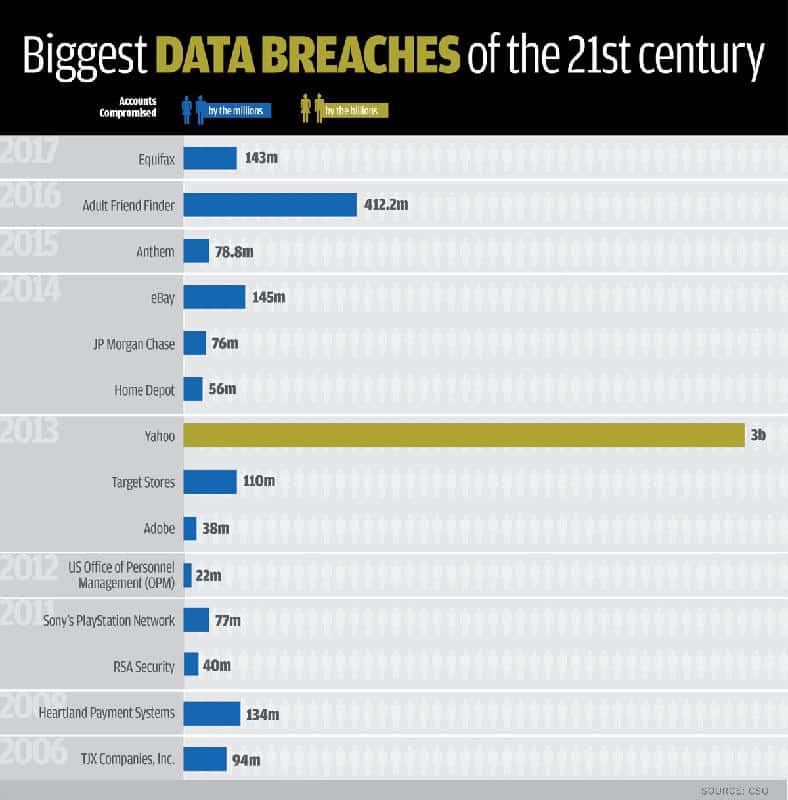
Four of the five largest data breaches have happened in the past few years. Yahoo’s biggest was upgraded in 2016 when it was announced that the breach, originally estimated to affect 1 billion accounts, exposed all 3 billion accounts. No. 4 on the list is the attack that captured 145 million data accounts from credit bureau Equifax. This doesn’t even count cybercrime, like the organizations in 150 countries ransomed by the WannaCry hack.
In a survey by KPMG, about 1 in 5 shoppers said they would completely stop visiting a retailer if they learned about a breach, and 1 in 3 said they would just take a break from shopping there for an unspecified amount of time. Yet over the past year, consumers have seen massive, successful cyberattacks on popular brands like Delta, Best Buy, Saks Fifth Avenue and Whole Foods, among many others. The scope of the problem has grown so overwhelming that consumers and businesses are desperate to find partners they can trust with their data.
We live in an Age of Disruption, which has both positive and negative aspects. The positive is the value creation by innovative concepts and business models, but the flip side of that is that technology is enabling malicious online actors who can do more damage faster than ever before.
The keys to staying ahead of cybercriminals and differentiating from competitors in the Age of Disruption turn out to be determined by a single path: proving that the organization can act as a trustworthy steward of stakeholder data.
5 Actions to Take ASAP
Here are some actions that a future-proofing organization can and should take as soon as possible:
1. Generate a customized vulnerability report
A good defense starts with a good understanding of what attackers want, what methods have been most effective for them, and what others in the industry are doing to prepare for them. Each company will have a unique vulnerability profile and strengths that hackers don’t know about. This report should explain and provide examples of phishing, malware, ransomware, cyber fraud, threat modeling, and social engineering.
2. Narrow the attack surface
Up to 90 percent of breaches enter organizations through communications channels, especially email-based phishing campaigns for credentials to launch a deeper attack. Most hackers aren’t targeting specific companies — they send bots to recon the entire internet and harvest the low-hanging fruit. Reducing the attack surface makes the organization invisible to many potential threats. Start with signature-based malware detection, behavioral-based analysis algorithms, and an evaluation routine to ensure security patches are updated across the network.
3. Establish multiple sites for backups
Not every breach begins with a malicious action. Data corruption, physical accidents, equipment failure, and acts of nature can expose an organization to critical data loss. Often, hackers quickly become aware of these situations and take advantage of them, doubling the damage. Make regular backups kept offline, with copies in the cloud for geo-failover.
4. Review social network privacy settings
Organizations can only be as safe as those who manage them, so the consumer level significantly impacts operations on every level. Facebook’s privacy issues matter more than ever for organizations trying to establish trust with their stakeholders. Conduct team member/volunteer training to audit privacy settings and install legitimate tracker blockers.
5. Investigate AI and machine learning for original security tools
Cybercriminals are already using AI and machine learning tools, so cybersecurity experts must enlist the aid of tech that hasn’t been invented yet to counteract those efforts. Organizations in every industry are testing out customized AI-enabled security applications tailored to their infrastructure weaknesses, as identified in the vulnerability report mentioned above.
The Cybersecurity Essentials
Despite the $96 billion that will be spent on cybersecurity this year, private data is still being exposed, and trillions have been siphoned off by malicious actors online. Financial loss due to cybercrime is on track to double by 2021, up to a $6 trillion drag on the world’s business community. In the years ahead, as brands compete increasingly to provide the best customer experience, one of the key elements of that experience will be the stewardship of customer data.
Leading organizations can take great strides in protecting themselves, their partners, and their customers by:
- Making a customized report of common attack vectors and a prioritized list of the organization’s vulnerabilities
- Reducing the likelihood of attacks using basic cybersecurity software and regular reviews of security patch updates
- Maintaining critical data backups offline and in multiple locations in the cloud
- Conducting security training for employees that includes managing privacy settings on social networks
- Outsourcing the development of security programming incorporating AI and machine learning
Cybercrime is not going away, and the streamlining of technology will make it easier for more people as time goes on. While successful organizations will always be a prime target for malicious actors, they can count on security-minded partners to think a few steps ahead and put preventative tech in place to minimize or eliminate these threats.



